Introduction
Software architecture for IoT systems determines whether Nigerian businesses deploy resilient, scalable solutions or struggle with connectivity failures and operational bottlenecks. While many organizations focus on selecting IoT devices and connectivity providers, the underlying software architecture often receives insufficient attention—yet it fundamentally shapes system reliability, maintenance costs, and business outcomes. A logistics company in Lagos may deploy thousands of tracking devices with universal SIM cards, but without proper software architecture, network transitions create data gaps, scaling becomes painful, and operational costs spiral out of control.
This comprehensive guide reveals software architecture principles specifically applicable to IoT deployments across Nigeria and Africa, where multinetwork connectivity, unreliable infrastructure, and distributed operations create unique technical challenges. Whether you’re building fleet management systems, agricultural monitoring platforms, or smart metering infrastructure, understanding how to architect IoT systems for African telecommunications environments ensures your investment delivers lasting value rather than accumulating technical debt.
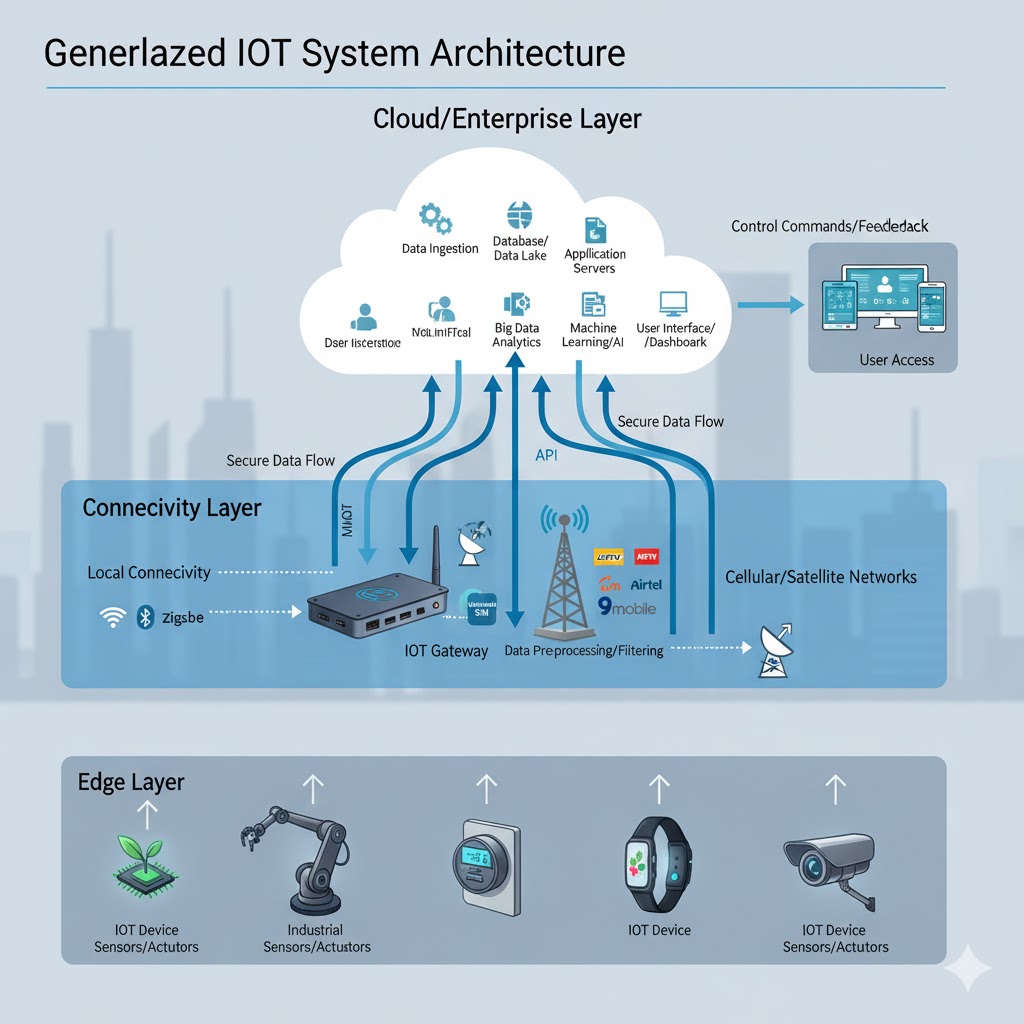
1. Why Software Architecture Matters More Than Device Selection
Nigerian businesses often prioritize hardware specifications and connectivity plans while treating software architecture as an afterthought. This approach creates expensive problems down the line: systems that can’t scale beyond pilot deployments, architectures requiring complete rewrites when requirements change, and operational complexity consuming engineering resources that should focus on business value.
The Hidden Cost of Poor Architecture
Operational Burden Compounds Over Time A Nigerian banking institution deployed 500 ATMs with IoT monitoring devices across multiple states. Their initial architecture directly connected each device to a central database without intermediate processing layers. This worked initially, but as the deployment scaled to 2,000 devices, database connection limits were reached, queries slowed dramatically, and the entire monitoring system became unreliable. Resolving this required a fundamental architectural redesign while supporting production operations—exponentially more expensive than building proper architecture initially.
Similar to the Netflix experience where edge systems handled operational burdens before architectural maturity, Nigerian IoT deployments face continuous operational challenges. Network interruptions across MTN, Airtel, Glo, and 9mobile require architecture anticipating connectivity failures rather than assuming reliable networks. Universal SIM cards provide connectivity redundancy, but software architecture must handle network transitions gracefully without data loss or service disruption.
Rigid Architecture Prevents Business Evolution An agricultural technology company built crop monitoring systems for Nigerian farms using hardcoded logic connecting sensors directly to visualization dashboards. When customers requested historical analysis, predictive analytics, and integration with farm management software, the architecture couldn’t accommodate these features without complete rewrites. The original architecture optimized for quick prototype deployment but created insurmountable barriers to business growth.
Good software architecture for IoT systems anticipates evolution. As one experienced architect noted about system design: “Someone’s ability to write high-quality code is entirely independent of their ability to create high-quality architecture.” Nigerian IoT projects succeed when architecture balances immediate delivery with future flexibility—solving today’s problems while creating better problems tomorrow.
Trading Problems: The Core Architectural Principle
Upgrading Your Problems Through Design Effective software architecture for IoT involves purposefully trading current problems for better ones. Consider a logistics company tracking vehicles across Nigeria. Initial architecture might poll devices every 30 seconds for location updates, consuming excessive cellular data and creating cost problems. Improved architecture implements event-driven reporting where devices transmit only when significant changes occur (route deviation, prolonged stops, geofence crossings), trading constant polling costs for more complex event detection logic.
This trade improves business outcomes: reduced data costs (40-60% savings), more intelligent alerting, and scalable architecture supporting thousands of additional vehicles without proportional cost increases. The new problem—implementing sophisticated event logic—proves far more manageable than the original problem of unsustainable data costs.
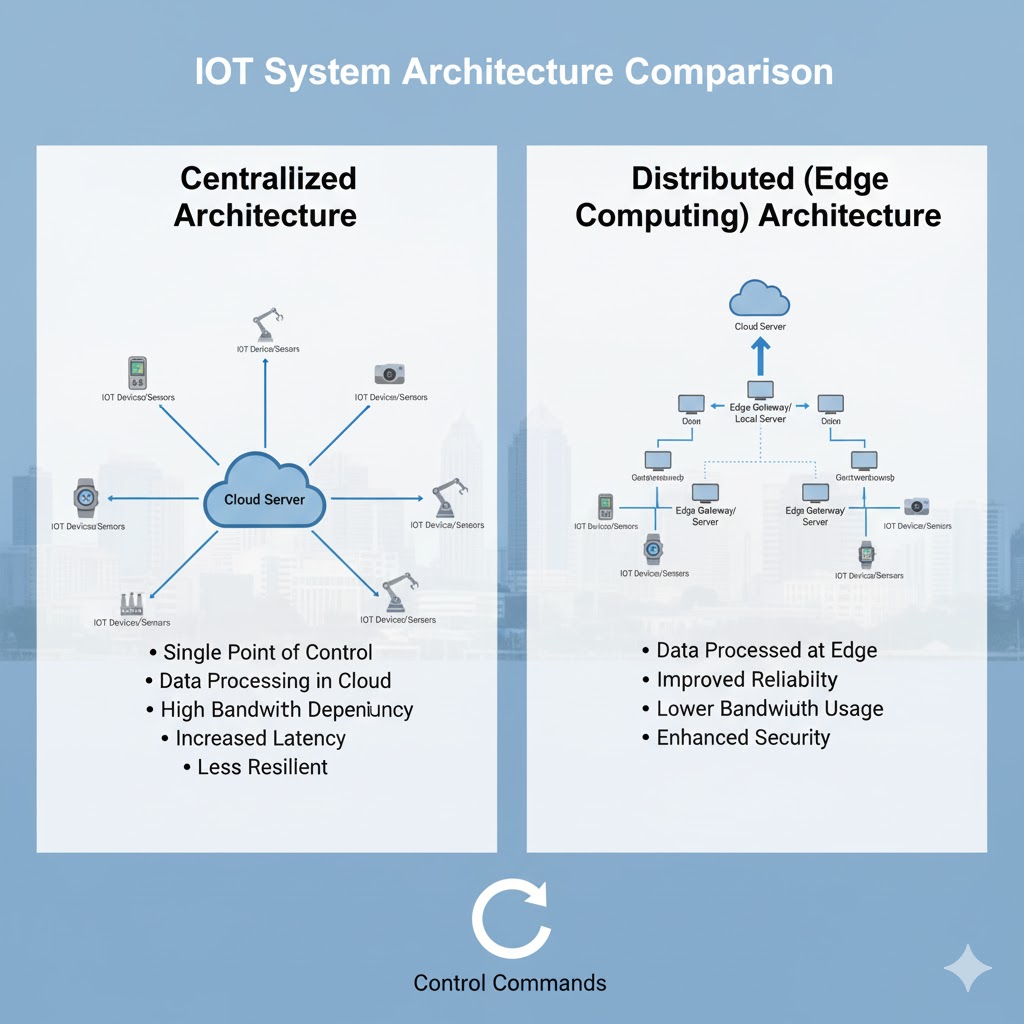
Infrastructure Tradeoffs: Cloud vs. Edge Computing Nigerian IoT deployments face unique infrastructure decisions. Pure cloud architectures depend entirely on cellular connectivity, making systems vulnerable to network outages and creating high data transmission costs. Pure edge computing architectures (processing everything locally on devices) limit analytics capabilities and complicate fleet management.
Hybrid architectures trading these limitations prove most effective for African telecommunications environments. Devices perform local processing and buffering, transmitting aggregated data and alerts via universal SIM cards when connectivity permits. This architecture trades implementation complexity for operational resilience—devices continue functioning during network interruptions, data costs decrease through intelligent aggregation, and cloud services focus on high-value analytics rather than real-time data processing.
2. Essential Architectural Patterns for Nigerian IoT Systems
Successful IoT systems in Nigeria require specific architectural patterns addressing unreliable connectivity, distributed operations, and scaling challenges unique to African telecommunications infrastructure. These patterns separate deployments that thrive from those that struggle operationally.
Circuit Breaker Pattern for Network Resilience
Preventing Cascading Failures Nigerian IoT systems interact with multiple external services: cellular networks (MTN, Airtel, Glo, 9mobile), cloud platforms, third-party APIs, and backend databases. When any dependency experiences problems, poorly architected systems propagate failures throughout the entire infrastructure. A slow database query delays all device communications; a cloud service timeout freezes the entire fleet management dashboard.
The circuit breaker pattern prevents these cascading failures by monitoring external service health and automatically “opening the circuit” when problems are detected—temporarily blocking requests to failing services while allowing the rest of the system to continue functioning. After a timeout period, the circuit “half-opens” to test if the service has recovered, automatically restoring full functionality when appropriate.
For GenYZ Solutions’ IoT deployments supporting FCMB and Wema Bank, circuit breakers ensure ATM monitoring continues even when specific backend services experience issues. If the central reporting database becomes slow, circuit breakers prevent all monitoring devices from overwhelming the database with retry attempts, instead buffering data locally and resuming transmission when the database recovers.
Event-Driven Architecture for Scalability
Decoupling Components for Growth Traditional request-response architectures become bottlenecks as Nigerian IoT deployments scale. Each device directly calling backend services creates tight coupling—system modifications require coordinating changes across devices, services, and databases simultaneously. This coupling slows development velocity and creates deployment risks.
Event-driven architectures decouple components through message queues or event streams. Devices publish events (location updates, sensor readings, alert conditions) to message queues without knowing which services consume them. Backend services subscribe to relevant events, processing them independently without direct device coordination. This pattern enables:
Horizontal Scaling: Add more message consumers to handle increased device volume without modifying device software Service Independence: Deploy new analytics services consuming existing event streams without affecting production systems Reliability Through Buffering: Message queues buffer events during service downtime, preventing data loss during infrastructure maintenance
A Lagos-based fleet management company utilizing this architecture scaled from 500 to 5,000 tracked vehicles with minimal backend modifications—additional message queue consumers handled increased event volume without requiring device firmware updates or system downtime.
Data Aggregation and Compression
Optimizing for African Network Costs Cellular data costs in Nigeria remain significant compared to developed markets. IoT architectures transmitting raw sensor data continuously create unsustainable operational expenses. Intelligent data aggregation and compression reduce transmission costs while maintaining analytical value.
Effective aggregation strategies include:
Time-Based Aggregation: Transmit average, minimum, and maximum sensor values over 5-minute windows rather than individual readings every 30 seconds Change-Based Transmission: Report only when values change beyond configured thresholds, eliminating redundant data for stable conditions Adaptive Sampling: Increase reporting frequency during interesting events (temperature spikes, unusual vibration) while reducing frequency during normal operations
Agricultural IoT projects in Nigeria implementing these patterns achieve 70-85% data transmission reductions without losing actionable insights. Universal SIM cards from GenYZ Solutions optimize costs further by automatically selecting the most cost-effective network for data transmission across MTN, Airtel, Glo, and 9mobile operators.
State Management and Synchronization
Handling Distributed Device State IoT devices across Nigeria operate in distributed environments with intermittent connectivity. Software architecture must handle state synchronization between devices, edge gateways, and cloud services—ensuring consistency despite network interruptions and varying latency.
Effective state management patterns:
Local State Authority: Devices maintain authoritative state for operational parameters, synchronizing to cloud services when connectivity permits rather than requiring constant cloud communication Conflict Resolution Strategies: Implement clear rules for resolving state conflicts when devices reconnect after extended offline periods (last-write-wins, timestamp-based merging, manual resolution for critical conflicts) State Versioning: Track state versions enabling detection of synchronization issues and preventing older state from overwriting newer updates
A Nigerian smart metering deployment uses this pattern enabling meters to function autonomously during network outages, synchronizing consumption data and configuration updates when connectivity restores via universal SIM cards providing multinetwork redundancy.
3. Building Resiliency Into IoT Architecture
Resiliency distinguishes successful Nigerian IoT deployments from those requiring constant operational intervention. African telecommunications infrastructure creates inherent unreliability—network interruptions, power outages, and infrastructure limitations are operational realities rather than exceptional circumstances requiring mitigation through architectural design.
Graceful Degradation Strategies
Maintaining Core Functionality During Failures Resilient IoT systems prioritize core functionality over complete feature sets during degraded conditions. A vehicle tracking system’s core function is location reporting; secondary features include diagnostics, driver behavior analysis, and maintenance scheduling. Architecture should ensure location tracking continues even when backend analytics services are unavailable.
Implementing graceful degradation:
Feature Tiering: Classify functionality by criticality, ensuring Tier 1 features (location, critical alerts) maintain operation even when Tier 2 (analytics) and Tier 3 (reporting) features fail Local Fallback Processing: Devices perform simplified processing locally when cloud services are unreachable, upgrading to sophisticated cloud-based processing when connectivity restores User Interface Adaptation: Dashboards indicate degraded operation modes, setting appropriate expectations while maintaining visibility into available data
This approach prevents complete system failures—users access critical capabilities even during infrastructure problems, maintaining operational value throughout incidents.
Data Buffering and Store-Forward
Preventing Data Loss During Connectivity Gaps Universal SIM cards from Genyz Solutions provide multinetwork connectivity across Nigerian operators, but even with network redundancy, temporary connectivity gaps occur. Software architecture must buffer data during these gaps, automatically resuming transmission when networks become available.
Effective buffering strategies include:
Intelligent Buffer Management: Prioritize critical data (security alerts, anomaly detections) over routine telemetry during connectivity constraints Compression Before Storage: Minimize device storage requirements through data compression, enabling longer offline operation periods Incremental Transmission: Resume data uploads from interruption points rather than retransmitting entire buffers, optimizing for limited bandwidth scenarios
An offshore oil platform monitoring system in the Gulf of Guinea uses these patterns to maintain operations during satellite communication interruptions. Devices buffer up to 72 hours of sensor data locally, automatically synchronizing when connectivity restores without operator intervention or data loss.
Automated Recovery and Self-Healing
Reducing Operational Burden Through Automation Manual intervention for every connectivity issue or device problem creates unsustainable operational costs for large Nigerian IoT deployments. Self-healing architectures detect problems and execute recovery procedures automatically, minimizing human intervention requirements.
Self-healing capabilities:
Automatic Device Restart: Detect unresponsive devices and execute remote restart procedures resolving transient software issues Network Switching Logic: Automatically switch between cellular networks when current connections degrade, leveraging universal SIM multinetwork capabilities Configuration Rollback: Detect failed configuration updates and automatically restore previous working configurations Alert Escalation: Route alerts through escalation paths ensuring critical issues receive attention when primary contacts are unavailable
These capabilities reduce operational overhead while improving system reliability—devices recover automatically from common failures while engineering resources focus on unique problems requiring human judgment.
4. Scalability Patterns for Growing IoT Deployments
Nigerian businesses often begin with pilot IoT deployments of 50-100 devices, intending to scale to thousands as business value proves out. Software architecture for IoT must accommodate this growth without requiring fundamental redesigns—initial architecture should anticipate scale even if starting small.
Horizontal Scaling for Backend Services
Adding Capacity Through Replication Horizontal scaling adds additional service instances handling increased load rather than upgrading individual servers (vertical scaling). This approach proves more cost-effective and resilient for IoT systems, as failure of individual service instances doesn’t impact overall system availability.
Architectural requirements for horizontal scaling:
Stateless Service Design: Backend services shouldn’t maintain session state, enabling requests to route to any available instance Distributed Data Stores: Utilize databases supporting horizontal scaling (sharding, replication) rather than single-server databases with capacity limits Load Balancing: Distribute requests across service instances based on current load, health checks, and geographic proximity
A Nigerian logistics company scaled their fleet tracking system from 500 to 8,000 vehicles using horizontal scaling patterns. Initial architecture utilized stateless API services and distributed databases, enabling capacity increases by adding servers rather than architectural rewrites. Universal SIM cards from Genyz Solutions ensured connectivity scaled proportionally without network coverage concerns across Nigerian states.
Microservices vs. Monolithic Architecture
Choosing Appropriate Service Boundaries Microservices architecture decomposes systems into independent services, each handling specific business capabilities. This enables independent deployment, technology diversity, and team autonomy. However, microservices introduce complexity through distributed system challenges—network communication, data consistency, operational overhead.
For Nigerian IoT deployments:
Favor Monoliths Initially: Start with well-structured monolithic applications during pilots and early deployments, avoiding premature microservices complexity Extract Services Based on Scaling Needs: Identify components requiring independent scaling (data ingestion, analytics, reporting) and extract them as separate services when scaling demands justify complexity Maintain Strong Service Contracts: Whether monolithic or microservices, define clear interfaces between components enabling future architectural evolution
A banking IoT application managing ATM connectivity across Nigeria started monolithically, extracting the real-time alerting service as microservice when alert volume justified dedicated infrastructure. This pragmatic approach balanced simplicity with scalability needs.
Database Sharding and Partitioning
Distributing Data for Performance and Scale As device counts grow, single-database architectures reach performance limits. Sharding distributes data across multiple databases, each handling a subset of total data volume. Effective sharding strategies for Nigerian IoT systems include:
Geographic Sharding: Partition data by Nigerian state or region, enabling regional databases serving local devices while reducing latency Device ID Sharding: Distribute devices across database shards using device identifier ranges or hash-based distribution Time-Based Partitioning: Historical data partitions by time periods, enabling efficient archival of old data while maintaining fast access to recent data
Agricultural monitoring systems covering farms across multiple Nigerian states utilize geographic sharding—northern farms connect to databases in Kano while southern farms use Lagos infrastructure. This reduces latency while enabling independent scaling based on regional device concentrations.
5. Security Architecture for IoT Systems
Security represents critical concern for Nigerian IoT deployments, particularly for banking, logistics, and industrial applications where compromised devices create financial and safety risks. Software architecture for IoT must embed security throughout rather than treating it as an add-on feature.
Defense in Depth Strategy
Multiple Security Layers Effective IoT security implements multiple protective layers ensuring breaches of individual layers don’t compromise entire systems. Security layers include:
Device Security: Secure boot processes, encrypted storage, tamper detection, and hardware security modules preventing unauthorized device access Communication Security: TLS encryption for all network communications, certificate-based authentication, and secure credential management Application Security: Input validation, authorization controls, and secure API design preventing application-layer attacks Infrastructure Security: VPN connectivity, network segmentation, and intrusion detection systems protecting backend infrastructure
GenYZ Solutions’ universal SIM cards support private APN configurations enabling secure, dedicated network paths between devices and backend services—critical for FCMB and Wema Bank IoT deployments where security requirements meet Nigerian Communications Commission (NCC) standards.
Certificate-Based Authentication
Moving Beyond Static Credentials Traditional IoT security using hardcoded passwords or API keys creates vulnerabilities—credentials leak through source code repositories, devices ship with default passwords, and credential rotation proves operationally challenging. Certificate-based authentication provides stronger security with operational manageability.
Certificate-based patterns:
Device Certificates: Each device receives unique certificates during manufacturing or provisioning, authenticating device identity during connections Certificate Rotation: Automated certificate renewal before expiration, ensuring continuous security without manual intervention Revocation Capabilities: Compromised device certificates can be revoked, preventing unauthorized access without affecting other devices
A Nigerian smart city project managing thousands of environmental sensors implements certificate-based authentication, enabling secure device communications while supporting remote device management through GenYZ Solutions’ SIM management platform.
Data Encryption and Privacy
Protecting Sensitive Information IoT systems collecting personal data, financial information, or commercially sensitive operational data must implement encryption protecting this information throughout its lifecycle—during transmission, processing, and storage.
Encryption strategies:
End-to-End Encryption: Data encrypted on devices before transmission, decrypted only in authorized backend services Field-Level Encryption: Sensitive fields encrypted individually, enabling analytics on non-sensitive data while protecting critical information Key Management: Secure key generation, distribution, rotation, and storage using hardware security modules or cloud key management services
Nigerian banking IoT applications processing financial data implement these patterns ensuring compliance with data protection regulations while maintaining system functionality.
6. Monitoring and Observability for IoT Operations
Software architecture for IoT systems must include comprehensive monitoring and observability enabling operations teams to understand system health, diagnose problems quickly, and optimize performance across distributed Nigerian deployments.
Three Pillars of Observability
Metrics, Logs, and Traces Effective observability combines three data types providing complete system visibility:
Metrics: Quantitative measurements of system behavior (device count, message throughput, error rates, latency percentiles) enabling real-time health monitoring and alerting Logs: Detailed event records supporting problem diagnosis and audit trails for compliance requirements Distributed Traces: Request flows across multiple services, revealing performance bottlenecks and failure points in complex architectures
Nigerian IoT deployments benefit from observability platforms aggregating data across devices, connectivity layers (universal SIM cards and cellular networks), edge services, and cloud infrastructure—providing unified visibility into distributed systems.
Proactive Alerting Strategies
Detecting Problems Before Impact Reactive monitoring alerts when systems fail; proactive monitoring detects degrading conditions before failures impact operations. Effective alerting strategies:
Anomaly Detection: Machine learning models identify unusual patterns indicating developing problems (gradual memory leaks, increasing error rates, device connectivity degradation) Threshold-Based Alerts: Configure alerts for critical metrics (95th percentile latency exceeding thresholds, device offline rates above acceptable levels) Alert Aggregation: Group related alerts preventing alert fatigue while ensuring visibility into systemic problems
A Lagos fleet management deployment uses proactive monitoring detecting universal SIM connectivity issues before they impact vehicle tracking, automatically switching problematic devices to alternative networks through GenYZ Solutions’ SIM management platform.
Dashboard Design for Operations
Actionable Visibility Operations dashboards must provide actionable information enabling rapid decision-making during incidents. Effective dashboard design:
Role-Based Views: Different stakeholders (executives, operations, engineering) require different information—tailor dashboards to specific roles Geographic Visualization: Map-based displays showing device distribution, connectivity status, and regional issues across Nigerian states Drill-Down Capabilities: High-level overviews with ability to investigate specific devices, networks, or time periods for detailed analysis
These patterns enable operations teams managing thousands of IoT devices across Nigeria to quickly identify and resolve issues minimizing business impact.
7. Practical Implementation Guidelines for Nigerian Businesses
Translating software architecture principles into successful Nigerian IoT deployments requires practical implementation guidelines addressing real-world constraints—limited technical resources, budget pressures, and timeline demands.
Start Simple, Architect for Growth
Avoiding Over-Engineering The principle “good architecture trades problems you have today for better problems tomorrow” means avoiding over-engineering. Don’t build systems for imaginary future problems; build for current needs while maintaining architectural patterns enabling future growth.
Practical approaches:
Pilot with Production Architecture: Even small pilots should use production-grade architecture—proper error handling, monitoring, security. Avoid prototype architecture requiring rewrites for production deployment Defer Optimization: Don’t prematurely optimize for scale. Deploy simple implementations and optimize when actual performance data reveals bottlenecks Document Architectural Decisions: Record why specific architectural choices were made, enabling future teams to evolve architecture intelligently
Leverage Managed Services and SaaS
Reducing Operational Burden Nigerian businesses often lack extensive DevOps resources. Managed services and SaaS platforms reduce operational complexity, enabling small teams to build sophisticated IoT systems:
Cloud Platforms: AWS IoT Core, Azure IoT Hub, Google Cloud IoT provide managed device connectivity, data routing, and basic analytics Managed Databases: Cloud database services handle scaling, backups, and maintenance automatically SIM Management Platforms: GenYZ Solutions’ platform manages universal SIM cards, network selection, and connectivity monitoring—eliminating need for in-house connectivity expertise
These services trade monthly operational costs for reduced engineering overhead and faster time-to-market—usually favorable tradeoffs for Nigerian businesses focused on business value rather than infrastructure management.
Partner with Connectivity Experts
Critical Role of Network Partners Software architecture proves ineffective without reliable connectivity. Universal SIM cards from Genyz Solutions provide multinetwork connectivity across MTN, Airtel, Glo, and 9mobile—but effective partnerships extend beyond SIM provisioning:
Architecture Consultation: Connectivity partners should advise on architectural patterns optimizing for Nigerian network characteristics Integration Support: Technical assistance integrating SIM management platforms with IoT applications Operational Support: Rapid response to connectivity issues minimizing business disruptions
GenYZ Solutions’ proven deployments supporting FCMB, Wema Bank, and enterprises across Nigeria demonstrate commitment to partnership beyond commodity SIM provisioning.
Conclusion: Building Resilient IoT Architecture with Genyz Solutions
Software architecture for IoT systems fundamentally determines success or failure of Nigerian deployments. While universal SIM cards provide essential multinetwork connectivity, robust architecture transforms connectivity into business value—systems that scale gracefully, operate reliably despite infrastructure challenges, and evolve as business requirements change.
Effective architecture trades current problems for better ones: replacing fixed infrastructure with elastic cloud capacity, substituting manual operations with automated recovery, and exchanging monolithic complexity with well-bounded microservices. These trades aren’t free—they introduce new challenges—but they upgrade problems from business-limiting to technically manageable.
Genyz Solutions combines multinetwork universal SIM cards with deep understanding of architectural patterns succeeding across African telecommunications environments. Our partnerships with FCMB, Wema Bank, and enterprises throughout Nigeria demonstrate our capability supporting mission-critical deployments where architecture and connectivity must work flawlessly together.
Whether you’re building fleet management systems, agricultural monitoring platforms, smart metering infrastructure, or banking IoT applications, Genyz Solutions provides the connectivity foundation and architectural consultation enabling resilient, scalable systems across Nigeria’s 36 states and beyond.
Begin Your IoT Architecture Journey
Don’t let poor architecture undermine your IoT investments. Contact Genyz Solutions for free consultation evaluating your architectural requirements. Our team combines connectivity expertise with software architecture knowledge, recommending patterns optimized for Nigerian deployments and providing universal SIM cards ensuring reliable multinetwork connectivity.
Visit www.genyzsolutions.com or call our Lagos office to discuss how proper software architecture and universal SIM connectivity can power your Nigerian IoT success.

